[Method] Get Any Microsoft Product Free
Lets start
PART 1
1. Go to ebay.com
2. Search for "Microsoft Products". (Suppose you chose a "gaming keyboard")
3. Select any product below $150, and tell the seller that "I am ready to buy, but just to make sure that I am getting the right thing, i want to know the PID number of the product".
4. Seller will mail you PID number.
Part 2
1. Call up microsoft customer service OR have a chat with their representative
2. I dont have the number byhearted so goto support.microsoft.com and find that out
3. Tell them that " I own this (the same) Gaming Keyboard, its broken, some of the keys are not working, I have done all the troubleshooting."
4. VOILA!, they will say that "Its ok, sir, we will send your another!"
5. YOUR DONE!!

How it works?
When they send you another keyboard, they would NOT ask you to return the existing broken keyboard, because the SHIPPING will cost them more than the price of the keyboard. So thats what is the loophole
Why till $150?
As i mentioned above, if the replacement product costs more than $150, then they will ask you to return the existing broken product at the time of delivery, which apperantly we dont have
Can I get caught?
NO!. Its done through complete legal way, I have already ordered 5 of them and have received 3 at my friend's place in US.
P.S = I don't know if this works these days but its tested by me before some times
Selling Methods cashout,ebay method,paypal carding etc...
To view links or images in signatures your post count must be 10 or greater. You currently have 0 posts.
PART 1
1. Go to ebay.com
2. Search for "Microsoft Products". (Suppose you chose a "gaming keyboard")
3. Select any product below $150, and tell the seller that "I am ready to buy, but just to make sure that I am getting the right thing, i want to know the PID number of the product".
4. Seller will mail you PID number.
Part 2
1. Call up microsoft customer service OR have a chat with their representative
2. I dont have the number byhearted so goto support.microsoft.com and find that out
3. Tell them that " I own this (the same) Gaming Keyboard, its broken, some of the keys are not working, I have done all the troubleshooting."
4. VOILA!, they will say that "Its ok, sir, we will send your another!"
5. YOUR DONE!!
How it works?
When they send you another keyboard, they would NOT ask you to return the existing broken keyboard, because the SHIPPING will cost them more than the price of the keyboard. So thats what is the loophole
Why till $150?
As i mentioned above, if the replacement product costs more than $150, then they will ask you to return the existing broken product at the time of delivery, which apperantly we dont have
Can I get caught?
NO!. Its done through complete legal way, I have already ordered 5 of them and have received 3 at my friend's place in US.
P.S = I don't know if this works these days but its tested by me before some times
Selling Methods cashout,ebay method,paypal carding etc...
To view links or images in signatures your post count must be 10 or greater. You currently have 0 posts.
![[Image: OGc6GPr.png]](http://i.imgur.com/OGc6GPr.png)
![[Image: 0izOL4F.gif]](http://i.imgur.com/0izOL4F.gif)
![[Image: b092eef785988a9f3a9ca669e4282f16.png]](http://i.gyazo.com/b092eef785988a9f3a9ca669e4282f16.png)
![[Image: f400e15b5a158fff8dfee6ec101bae29.png]](http://i.gyazo.com/f400e15b5a158fff8dfee6ec101bae29.png)
![[Image: Mining-social-media-gold.png]](http://socialleadfreak.com/wp-content/uploads/2013/04/Mining-social-media-gold.png)
![[Image: 1UgMgdh.png]](http://i.imgur.com/1UgMgdh.png)
![[Image: jfi7cdr-435f84d.png]](http://img96.xooimage.com/files/8/f/8/jfi7cdr-435f84d.png)
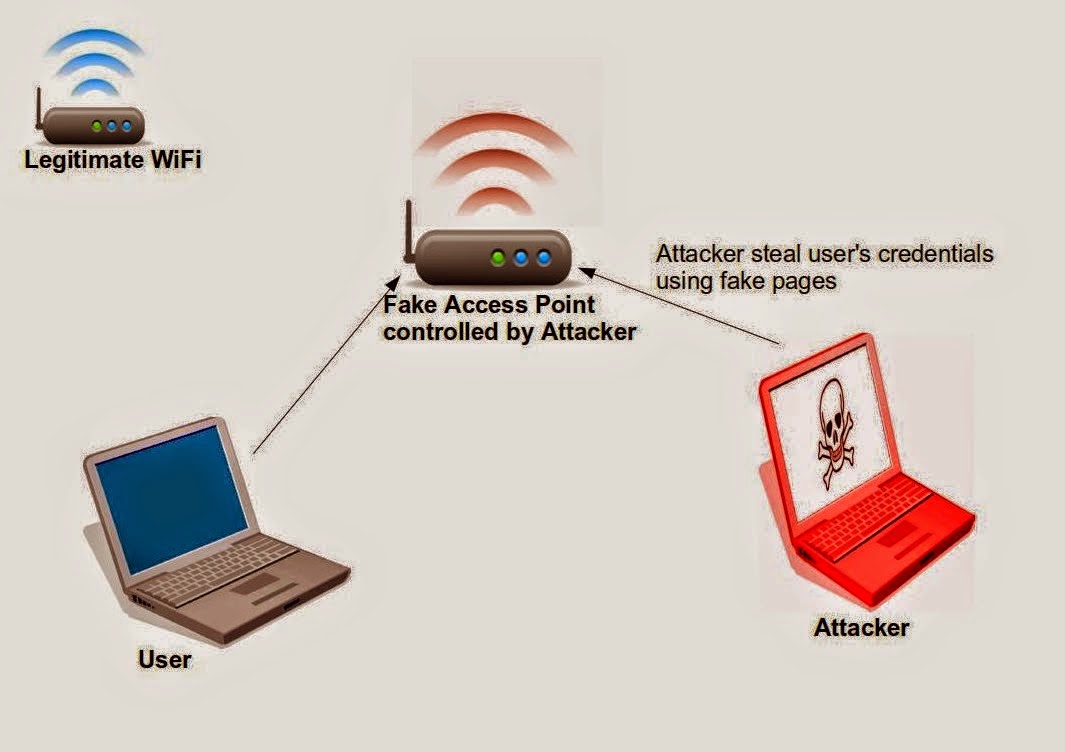

![[Image: pHjtq62.png]](http://i.imgur.com/pHjtq62.png)
![[Image: Ke5WbRJ.png]](http://i.imgur.com/Ke5WbRJ.png)
![[Image: X9fx0aG.png]](http://i.imgur.com/X9fx0aG.png)
![[Image: GGq6QLN.png]](http://i.imgur.com/GGq6QLN.png)
![[Image: 0u34Tb7.png]](http://i.imgur.com/0u34Tb7.png)
![[Image: OHAJvdL.png]](http://i.imgur.com/OHAJvdL.png)
![[Image: hkrVqVf.png]](http://i.imgur.com/hkrVqVf.png)
![[Image: pVY7vlI.png]](http://i.imgur.com/pVY7vlI.png)
![[Image: EuzvGer.png]](http://i.imgur.com/EuzvGer.png)
![[Image: UrCM3fN.png]](http://i.imgur.com/UrCM3fN.png)
![[Image: ewV9fI4.png]](http://i.imgur.com/ewV9fI4.png)
![[Image: NBopened.png]](https://dl.dropbox.com/u/18819048/AF%20TUTS/DNS/NBopened.png)
![[Image: NBfinished.png]](https://dl.dropbox.com/u/18819048/AF%20TUTS/DNS/NBfinished.png)
![[Image: CP.png]](https://dl.dropbox.com/u/18819048/AF%20TUTS/DNS/CP.png)
![[Image: NASC.png]](https://dl.dropbox.com/u/18819048/AF%20TUTS/DNS/NASC.png)
![[Image: selecprop.png]](https://dl.dropbox.com/u/18819048/AF%20TUTS/DNS/selecprop.png)
![[Image: netprops.png]](https://dl.dropbox.com/u/18819048/AF%20TUTS/DNS/netprops.png)










![[Image: offlineb_copy-700.jpg]](http://leecoleonline.com/teka/wp-content/uploads/2015/07/offlineb_copy-700.jpg)




